By default the SSL protocol encrypts data by using CBC mode with chained initialization vectors. This allows an attacker, which is has gotten access to an HTTPS session via man-in-the-middle (MITM) attacks or other means, to obtain plain text HTTP headers via a blockwise chosen-boundary attack (BCBA) in conjunction with Javascript code that uses the HTML5 WebSocket API, the Java URLConnection API, or the Silverlight WebClient API. This vulnerability is more commonly referred to as Browser Exploit Against SSL/TLS or “BEAST”.
1. Use this tool to test if your server is vulnerable: https://www.ssllabs.com/ssltest/analyze.html
2. Download IISCrypto from this site: https://www.nartac.com/Products/IISCrypto/Default.aspx
3. Install and run IISCrypto
4. Click the “BEAST” button in the Templates section and click apply
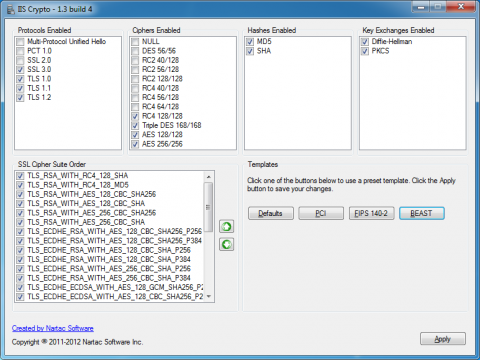
5. Restart the server